Site-to-site connectivity
BetaFeature availability
| WARP modes | Zero Trust plans |
|---|---|
| Gateway with WARP | All plans |
| System | Availability |
|---|---|
| Windows | ❌ |
| macOS | ❌ |
| Linux | ✅ |
| iOS | ❌ |
| Android | ❌ |
| ChromeOS | ❌ |
Cloudflare WARP Connector is a piece of software 1 that enables site-to-site, bidirectional, and mesh networking connectivity without requiring changes to underlying network routing infrastructure. WARP Connector establishes a secure Layer 3 connection between a private network and Cloudflare, allowing you to:
- Connect two or more private networks to each other.
- Connect IoT devices that cannot run external software, such as printers and IP phones.
- Filter and log server-initiated traffic, such as VoIP and SIP traffic.
- Apply Zero Trust security policies based on the source IP of the request.
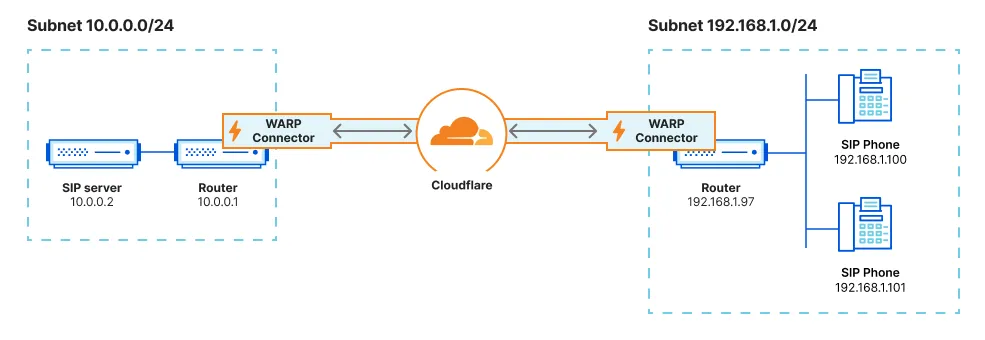
As shown in the diagram, WARP Connector acts as a router for a subnet within the private network to on-ramp and off-ramp traffic through Cloudflare. All devices on the subnet can access any services connected to Cloudflare, and all devices connected to Cloudflare can access any services on the subnet. Each subnet runs a WARP Connector on a designated Linux machine (typically the default gateway router), but other devices on the network do not need to install software.
This guide will cover how to connect two independent subnets, for example 10.0.0.0/24 and 192.168.1.0/24.
- A Linux host 2 on each subnet
- Verify that your firewall allows inbound/outbound traffic over the WARP IP addresses, ports, and domains.
Create a new service token and copy its Client ID and Client Secret. WARP Connector will use this service token to authenticate with your Zero Trust organization.
Next, create a device enrollment rule that allows the WARP Connector to authenticate:
-
In Zero Trust, go to Settings > WARP Client.
-
In the Device enrollment card, select Manage.
-
Select Add a rule.
-
Name the rule.
-
For Rule action, select Service Auth.
-
Configure the following fields:
Selector Value Service Token <SERVICE-TOKEN-NAME> -
Select Save.
All WARP Connector and WARP client devices in your Zero Trust organization have the same local IP address by default. To route traffic between various WARP devices, you must allow Cloudflare to assign a unique CGNAT IP to each device.
-
In Zero Trust, go to Settings > Network.
-
Enable Proxy.
-
Enable Warp to Warp. This allows Cloudflare to route traffic to the CGNAT IP space.
-
Next, go to Settings > WARP Client.
-
Enable Override local interface IP.
-
Check your Split Tunnel configuration and ensure that the CGNAT IP space (
100.96.0.0/12) routes through WARP.For example, if you are using Exclude mode, delete
100.64.0.0/10from the list and re-add100.64.0.0/11and100.112.0.0/12.
Each subnet must run its own WARP Connector on a Linux host. Installing on your router is the simplest setup, but if you do not have access to the router, you may choose any other machine on the subnet.
In this example, we will create a WARP Connector for subnet 10.0.0.0/24 and install it on 10.0.0.1. We will then create a second WARP Connector for subnet 192.168.1.0/24 and install it on 192.168.1.97.
-
In Zero Trust, go to Network > Tunnels.
-
Select Create a tunnel.
-
For the connector type, select WARP. Select Next.
-
A window will appear with a list of prerequisites. Select Confirm to continue.
-
Give the tunnel any name (for example,
Subnet-10.0.0.0/24) and select Save tunnel. -
Select the operating system of your host machine.
-
Copy-paste the command into a terminal window and run the command. WARP Connector software is now installed, but not yet connected to Cloudflare.
-
To authenticate the WARP Connector to your Zero Trust organization:
- Create an
mdm.xmlfile in/var/lib/cloudflare-warpusing any text editor:
Terminal window $ cd /var/lib/cloudflare-warp$ sudo vim mdm.xml- Add the following text to the file. Make sure to fill in your team name, the Client ID and Client Secret of your service token, and the WARP Connector token value (shown in the dashboard). As soon as you save this file, WARP will automatically register with the provided credentials.
<dict><key>organization</key><string>myteam</string><key>auth_client_id</key><string>b33d5a65a6e801cd875scefff5908457f29.access</string><key>auth_client_secret</key><string>cdb5fa2721018c39cfaf8ec7fca9b5f62860ff5c584a89121241c6d0c83878124591cce23</string><key>warp_connector_token</key><string>fVTLilTWgMiF3TMxTIMM3nMU2NsixOYTTDHW1IamOMyORL0Y0jUcMWAoZDZhVhLVdn2pTDhy0VFRWZdE22rQCFNN6jQUoOx0eIV0ehcj5RyTZl5PYRwU25wMMi0kDGUS2XZn5W0eJS3mZXS9DkUTJatMNiMZDtNb1TmtmMptENJ20WY0NmdYmIBLoVhtToFichIjtiMnTZIMMOYOGZmpATzzEm2MjhnC6tWMHwNwFGhoIN==</string></dict>- Verify the registration:
Terminal window $ warp-cli accountAccount type: TeamDevice ID: f174e90a-fafe-4643-bbbc-4a0ed4fc8415Public key: 4w5uugfh0q03nrmcn95ltfzeghfzuhl75o7pruyd0h7z9ar9x6doxwq50aszar5kdAccount ID: 699d98642c564d2e855e9661899b7252Organization: myteamTroubleshoot missing registration
If the registration did not go through, try the following troubleshooting strategies:- Ensure that
mdm.xmlis formatted correctly and stored in/var/lib/cloudflare-warp. - Ensure that you have a device enrollment rule with the Service Auth action (not Allow).
- Restart the WARP systemd service:
Terminal window $ sudo systemctl restart warp-svc.service - Clear an old registration and trigger WARP to re-register:
Terminal window $ sudo warp-cli delete - Review your WARP daemon logs for information about why the registration is failing.
- Verify that WARP is connected to Cloudflare:
Terminal window $ warp-cli statusStatus update: ConnectedSuccessTroubleshoot connection
If WARP is disconnected, try the following troubleshooting strategies:
-
Run
warp-cli connect. -
If your private network uses a firewall to restrict Internet traffic, ensure that it allows the WARP ports and IPs.
-
Review your WARP daemon logs for information about why the connection is failing.
- Create an
- Select Next.
- In CIDR, enter the private IPv4 address range that you wish to route through this WARP Connector (for example,
10.0.0.0/24). WARP Connector does not currently support IPv6 routes.
-
Select Save Tunnel.
-
In your Split Tunnel configuration, ensure that your CIDR is routing through the WARP tunnel. For instructions on how to do this, refer to Route private network IPs through WARP.
The
10.0.0.0/24WARP Connector is now connected to Cloudflare.flowchart LR subgraph subnet1[Subnet 10.0.0.0/24] router1["Device running WARP Connector 10.0.0.1"] end router1<-->C((Cloudflare)) -
Repeat these steps to install an additional WARP Connector on subnet
192.168.1.0/24. You can reuse the service token, but you will need to create a new tunnel and MDM file.flowchart LR subgraph subnet1[Subnet 10.0.0.0/24] router1["Device running WARP Connector #1 10.0.0.1"] end subgraph subnet2[Subnet 192.168.1.0/24] router2["Device running WARP Connector #2 192.168.1.97"] end router1<-->C((Cloudflare))<-->router2
Run the following commands on the machine where you installed WARP Connector. You will need to configure the host machine on each subnet.
-
Enable IP forwarding:
Terminal window $ sudo sysctl -w net.ipv4.ip_forward=1Save configuration to persist after reboot
Terminal window $ echo 'net.ipv4.ip_forward = 1' | sudo tee -a /etc/sysctl.d/99-warp-svc.conf$ sudo sysctl -p /etc/sysctl.d/99-warp-svc.conf
-
WARP’s virtual interface has a maximum transmission unit (MTU) of 1280 bytes, whereas the standard Ethernet MTU is 1500 bytes. To avoid dropping packets that exceed 1280 bytes, clamp the maximum segment size (MSS) of the host machine so that incoming payloads are less than the MTU of WARP:
Terminal window $ sudo iptables -t mangle -A FORWARD -i CloudflareWARP -p tcp -m tcp --tcp-flags SYN,RST SYN -j TCPMSS --clamp-mss-to-pmtu$ sudo iptables -t mangle -A FORWARD -o CloudflareWARP -p tcp -m tcp --tcp-flags SYN,RST SYN -j TCPMSS --clamp-mss-to-pmtuSave configuration to persist after reboot
- Create a bash script that writes the
iptablerules to a file:
Terminal window echo '#!/bin/bash# Define your rulesRULES=("-A FORWARD -i CloudflareWARP -p tcp -m tcp --tcp-flags SYN,RST SYN -j TCPMSS --clamp-mss-to-pmtu""-A FORWARD -o CloudflareWARP -p tcp -m tcp --tcp-flags SYN,RST SYN -j TCPMSS --clamp-mss-to-pmtu")# Apply the rulesfor rule in "${RULES[@]}"; doiptables -t mangle $ruledone# Save the rulesiptables-save > /etc/iptables/rules.v4' | sudo tee /usr/local/bin/apply_iptables_rules.sh- Run the script:
Terminal window $ sudo chmod +x /usr/local/bin/apply_iptables_rules.sh$ sudo /usr/local/bin/apply_iptables_rules.sh- Create a systemd service to restore the rules at startup:
Terminal window echo '[Unit]Description=Load iptables rules at startup[Service]Type=oneshotExecStart=/sbin/iptables-restore < /etc/iptables/rules.v4[Install]WantedBy=multi-user.target' | sudo tee /etc/systemd/system/iptables-persistent.service - Create a bash script that writes the
Depending on where you installed the WARP Connector, you may need to configure other devices on the subnet to route traffic through WARP Connector.
If you installed WARP Connector on your router, no additional configuration is necessary. All traffic will use the router as the default gateway.
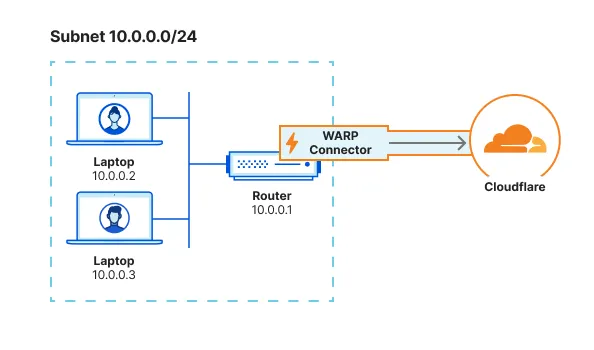
If you have access to the router but installed WARP Connector on another machine, you can configure the router to forward traffic to the WARP Connector. This typically involves adding a static route for the destination IPs that you want to connect to through Cloudflare. Refer to your router’s documentation for specific instructions on how to add an IP route.
For example, if you are on subnet 10.0.0.0/24 and want to reach applications behind subnet 192.168.1.0/24, add a rule that routes 192.168.1.0/24 to the WARP Connector IP (10.0.0.100 in the diagram below). When a device sends a request to 192.168.1.0/24, the router will first redirect the traffic to the WARP Connector machine. WARP Connector encrypts the traffic, changes its destination IP to the WARP ingress IP, and sends it back to the router. The router will now forward this encrypted traffic to Cloudflare.
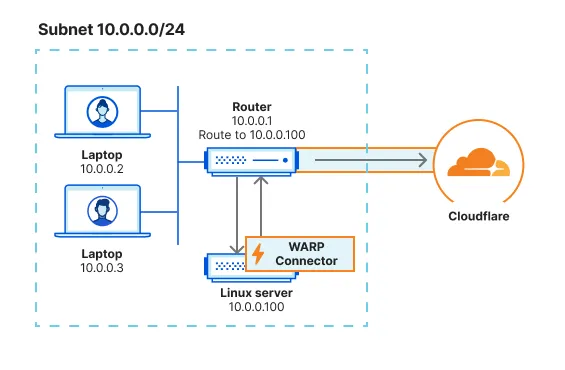
If you do not have access to the router, you will need to configure each device on the subnet to egress through the WARP Connector machine instead of the default gateway.
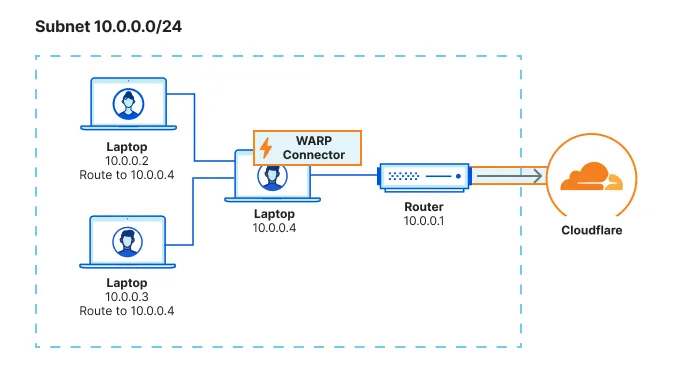
You can configure all traffic on a device to egress through WARP Connector with its local source IP. All traffic will be filtered by your Gateway network policies.
$ sudo ip route add default via <WARP-CONNECTOR-IP> dev eth0 metric 101Ensure that the metric value is lower than other default gateways. To verify that WARP Connector is now the preferred default gateway, run ip route get <DESTINATION-IP>.
$ sudo route -n change default <WARP-CONNECTOR-IP> -interface en0route /p add 0.0.0.0 mask 0.0.0.0 <WARP-CONNECTOR-IP> metric 101You can configure only certain routes to egress through WARP Connector. For example, you may only want to filter traffic destined to internal applications and devices, but allow public Internet traffic to bypass Cloudflare.
$ sudo ip route add <DESTINATION-IP> via <WARP-CONNECTOR-IP> dev eth0$ sudo route -n add -net <DESTINATION-IP> <WARP-CONNECTOR-IP>route /p add <DESTINATION-IP> mask 255.255.255.255 <WARP-CONNECTOR-IP>To validate subnet routing, check your routing table and ensure that traffic is routing through the CloudflareWARP virtual interface.
You can now test the connection between the two subnets. For example, on the 10.0.0.2 device run ping 192.168.1.100.
flowchart LR
subgraph subnet1[Subnet 10.0.0.0/24]
device1["Device
10.0.0.2"]--"ping
192.168.1.100"-->router1["Device running
WARP Connector
10.0.0.1"]
end
subgraph subnet2[Subnet 192.168.1.0/24]
router2["Device running
WARP Connector
192.168.1.97"]-->device2["Device
192.168.1.100"]
end
router1-->C((Cloudflare))-->router2
-
WARP Connector is an extension of the WARP client. ↩
-
Check the system requirements. Package dependencies are the following:
curl,gpg,iptables,iptables-persistent,lsb-core, andsudo. ↩